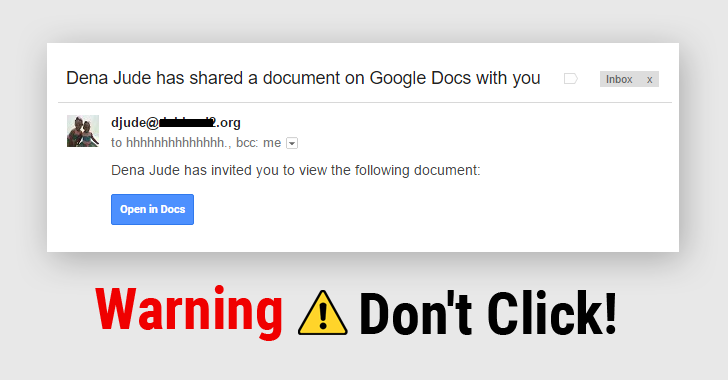
Hello Guys , Welcome To Hax4Us
| Hax4Us |
Yes , Iss App Ko Koi Bhi Use Kar Sakta Hai Iske liye koi special knowledge ki need nhi hai...
Name of application is APK EDITOR PRO ...
Ab Iss App ki help se hum kisi dusri app ka naam , icon ya logo , package name and or bhi bahut saari things modify kar sakte hai..
How To Use ?
Iske Use Ka ek simple demo video banayi hai jise aap niche dekh sakte hai.
Agar post me video nahi chal pata rahi hai to aap niche link par bhi click karke video dekh sakte hai.
Click Here To Watch
How To Download ?
APK EDITOR PRO ko play store se ya niche link par click karke bhi download kar sakte hai.......
Click Here To Download