|
| Thanks To THN |
Initially thought to be 600,000 users, the number of Android users who have mistakenly downloaded and installed malware on their devices straight from Google Play Store has reached 2 Million.
Yes, about 2 Million Android users have fallen victim to malware hidden in over 40 fake companion guide apps for popular mobile games, such as Pokémon Go and FIFA Mobile, on the official Google Play Store, according to security researchers from Check Point.
Dubbed FalseGuide by the Check Point researchers, the malware creates a "silent botnet out of the infected devices" to deliver fraudulent mobile adware and generate ad revenue for cybercriminals.
Nearly 2 Million Android Users Infected!
While initially it was believed that the oldest instance of FalseGuide was uploaded to the Google Play in February and made its way onto over 600,000 devices within two months, further in-depth analysis by researchers revealed more infected apps which date back to November 2016.
"Since April 24, when the article below was first published, Check Point researchers learned that the FalseGuide attack is far more extensive than originally understood," Check Point researchers wrote in a blog post.
"The apps were uploaded to the app store [Google Play Store] as early as November 2016, meaning they hid successfully for five months, accumulating an astounding number of downloads."
Russian connection with FalseGuide
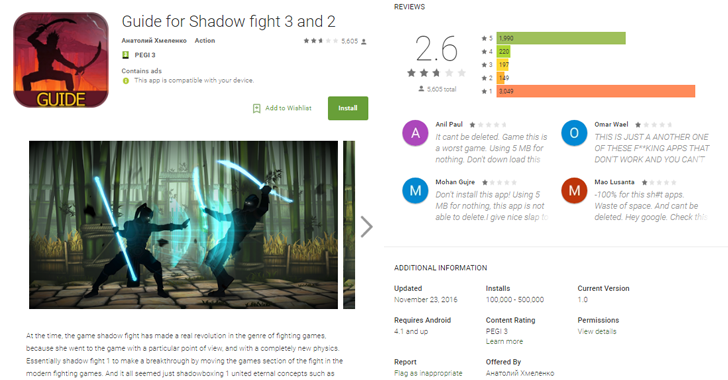
Check Point researchers discovered five additional apps containing the FalseGuide malware on Google Play Store, developed by "Anatoly Khmelenko" (translated from Russian Анатолий Хмеленко).
Also, the first batch of malicious apps was submitted under the Russian names of two fake developers, Sergei Vernik and Nikolai Zalupkin, which suggests the malware is of Russian origin.
FalseGuide attempts to turn infected devices into a botnet that could allow its operator to control the devices without the knowledge of the device owners.
Here's How FalseGuide Works:
The malware then registers itself with Firebase Cloud Messaging – a cross-platform messaging service that allows app developers to send messages and notifications.
Once subscribed to this service, FalseGuide can allow the attackers to send messages containing links to additional malware and install them to the infected device, enabling attackers to display illegitimate pop-up ads out of context and generate revenue.
Depending on their objectives, the attackers could also inject highly malicious code into an infected device to root it, conduct a Distributed Denial of Service (DDoS) attack, or even penetrate private networks.
Google Removed the Malware hidden Apps, but are you Clean?
Check Point has provided a full list of malicious apps hiding FalseGuide, which posed as guides for FIFA Mobile, Criminal Case, Super Mario, Subway Surfers, Pokemon Go, Lego Nexo Knights, Lego City My City, Ninjago Tournament, Rolling Sky, Amaz3ing Spider-Man, Drift Zone 2, Dream League Soccer, and many more.
Check Point researchers notified Google about FalseGuide in February, after which the company silently removed the malware apps from the Play Store.
But despite being removed, the malicious apps are likely still active on a number of devices, leaving Android users open to cyber attacks.
"Mobile botnets are a growing trend since early last year, growing in both sophistication and reach," CheckPoint said. "This type of malware manages to infiltrate Google Play due to the non-malicious nature of the first component, which only downloads the actual harmful code."
How to Protect yourself against such Malware
There are standard protection measures you need to follow to remain unaffected:
- Always download apps which are from trusted and verified developers and stick to trusted sources, like Google play Store and the Apple App Store.
- Always verify app permissions before installing apps. If any app is asking more than what it is meant for, just do not install it.
- Keep a good antivirus app on your device that can detect and block such malware before it can infect your device. Always keep the app up-to-date.
- Do not download apps from third party source. Although in this case, the app is being distributed through the official Play Store, most often such malware are distributed via untrusted third-party app stores.
- Avoid unknown and unsecured Wi-Fi hotspots and Keep your Wi-Fi turned OFF when not in use.
- Be careful which apps you give administrative rights to. Admin rights are powerful and can give an app full control of your device.
- Never click on links in SMS or MMS sent to your mobile phone. Even if the email looks legit, go directly to the website of origin and verify any possible updates.